StrongSwan Android IKEv2 PSK unlocks a world of secure network access. This comprehensive guide delves into the intricacies of configuring, securing, and optimizing this powerful VPN solution for Android devices. We’ll explore its potential, covering everything from fundamental setup to advanced troubleshooting and practical examples.
Imagine seamless connectivity, enhanced security, and optimized performance. This combination of technologies provides a robust and flexible VPN solution for various use cases, from personal privacy to enterprise networking. Understanding the nuances of StrongSwan, Android IKEv2, and PSK will empower you to leverage its full potential.
Introduction to StrongSwan Android IKEv2 PSK
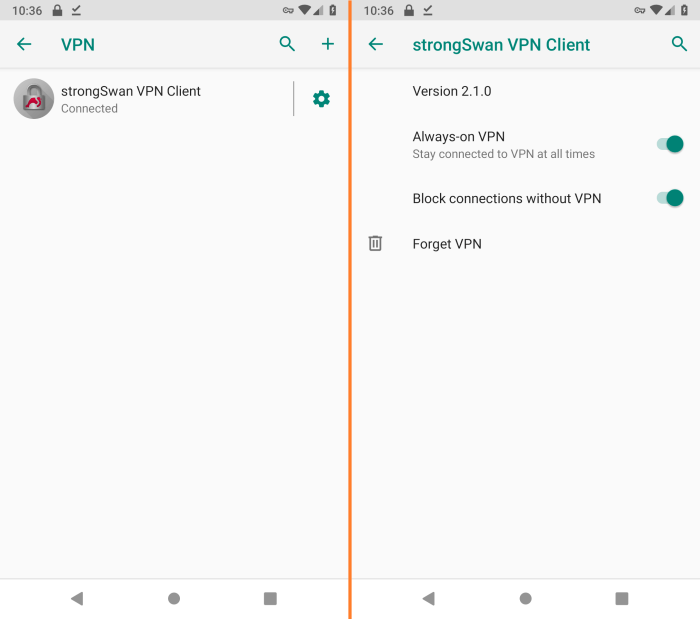
StrongSwan is a powerful open-source implementation of the Internet Key Exchange (IKE) protocol suite, widely recognized for its versatility and security. Android, the prevalent mobile operating system, offers a robust platform for various networking functionalities. IKEv2 is a modern IKE protocol designed for mobile environments, emphasizing enhanced performance and mobility. Pre-shared keys (PSK) provide a straightforward yet secure method of authentication in VPN connections.
Combining these components unlocks a secure and efficient VPN solution for Android devices.The combination of StrongSwan, Android’s IKEv2 support, and PSK authentication offers a highly secure and flexible solution for establishing VPN tunnels on Android devices. This combination is particularly useful for scenarios requiring a robust, yet user-friendly, VPN experience. The simplicity of PSK authentication simplifies the setup process, while the robust security of IKEv2 ensures a reliable and private connection.
Significance and Use Cases
StrongSwan, Android IKEv2, and PSK authentication together provide a compelling solution for various use cases. This combination is particularly beneficial for individuals or organizations requiring secure remote access to internal networks, ensuring data privacy and integrity during transit. It’s highly applicable for accessing company resources from mobile devices, securing personal Wi-Fi hotspots, or creating a secure tunnel for remote work or gaming.
Key Features and Protocol Overview
| Protocol | Description | Key Feature | Use Case |
|---|---|---|---|
| IKEv2 | Internet Key Exchange version 2, a modern protocol designed for mobility and efficiency. | Optimized for mobile environments, supporting seamless connectivity transitions and faster connection times. | Remote access to internal networks, secure Wi-Fi hotspots, and remote work scenarios. |
| StrongSwan | Open-source implementation of IKE protocols, offering a versatile and configurable solution. | Extensive customization options, supporting various security mechanisms and configurations. | Customizable VPN solutions, especially for environments requiring granular control over security parameters. |
| PSK | Pre-shared key authentication, a simple yet secure method to verify identities. | Ease of setup and management, ideal for scenarios requiring a straightforward authentication process. | Personal VPNs, guest Wi-Fi networks, and scenarios where user-friendliness is paramount. |
This table provides a concise overview of the protocols and their associated features, clearly demonstrating the utility of each component in creating a secure and user-friendly VPN solution. The combination of these components makes StrongSwan Android IKEv2 PSK an attractive option for a wide range of users and organizations.
Configuration and Setup
Unlocking the power of StrongSwan on Android requires a well-orchestrated setup process, akin to tuning a finely crafted instrument. This involves carefully configuring the IKEv2 protocol and employing a Pre-Shared Key (PSK) for secure communication. This meticulous process guarantees a robust and reliable connection, essential for any demanding network task.Navigating the configuration process is simplified by a structured approach, focusing on the key components and their interplay.
We’ll delve into the essential configurations for IKEv2 and PSK, providing practical examples to guide you. Furthermore, a comparative table will highlight different IKEv2 options, including the vital PSK aspect. This comprehensive approach equips you with the tools to confidently configure StrongSwan on your Android devices.
IKEv2 Configuration Details
The IKEv2 configuration, the cornerstone of secure communication, demands specific parameters for optimal functionality. These parameters ensure the connection’s integrity and security. Correct configuration settings prevent connectivity issues and ensure seamless data transfer.
PSK Configuration
The Pre-Shared Key (PSK) is the bedrock of security in this setup. It acts as a secret password, authenticating the devices and ensuring only authorized entities can establish the connection. A robust PSK is paramount to safeguarding sensitive data. This section will detail how to securely configure this crucial component.
- Generating a strong PSK: A robust PSK is critical. A randomly generated, complex string with upper and lowercase letters, numbers, and symbols is ideal. Avoid using easily guessable or predictable strings.
- Storing the PSK securely: Never hardcode the PSK within the configuration file. Instead, store it in a secure environment, such as a dedicated configuration file or a protected system variable.
Typical Configuration Files for StrongSwan Android IKEv2 PSK
The configuration files, acting as blueprints for the connection, contain the necessary parameters for the StrongSwan setup. These files dictate how IKEv2 and PSK interact to establish a secure tunnel.“`# Sample StrongSwan configuration file (strongswan.conf)config setup conn android_ikev2 authbypsk = yes left =
Comparison of IKEv2 Configuration Options (Including PSK)
A comparison table aids in understanding the different configuration options for IKEv2, especially when using PSK. It highlights the pros and cons of each option, facilitating informed decisions.
| Configuration Option | Description | Pros | Cons |
|---|---|---|---|
| PSK | Pre-Shared Key authentication | Simple to implement, widely used | Security risk if the key is compromised |
| Certificate-based authentication | Uses digital certificates for authentication | More secure than PSK | More complex to implement, requires certificate management |
| EAP (Extensible Authentication Protocol) | Provides flexibility for various authentication methods | Highly adaptable, supports different authentication methods | Can be complex to configure and maintain |
Security Considerations
Fortifying your StrongSwan Android IKEv2 PSK setup is paramount. A robust security posture isn’t just a good idea; it’s a necessity. Compromised VPN connections can expose sensitive data and potentially cripple your network. Let’s dive into the critical security best practices for your StrongSwan Android IKEv2 PSK configuration.Protecting your VPN connection requires meticulous attention to detail. The security of your network hinges on the strength and management of your pre-shared key (PSK).
A weak or carelessly handled PSK can quickly become a vulnerability. Let’s explore these crucial elements.
Strong PSK Generation and Management
A robust PSK is the cornerstone of your security. A strong PSK is long, complex, and random. Avoid easily guessable phrases or patterns. A strong PSK should be a sequence of random characters, ideally incorporating upper and lowercase letters, numbers, and symbols.Ideally, use a dedicated PSK generation tool to create a truly random key. These tools often employ cryptographic algorithms to produce keys that are extremely difficult to crack.
Never reuse PSKs across different networks or systems. A single compromised key can potentially expose multiple systems.
Potential Security Vulnerabilities and Mitigation Strategies
Several potential vulnerabilities can compromise your StrongSwan Android IKEv2 PSK setup. One significant concern is the risk of PSK exposure. Hackers could potentially intercept the PSK during transmission or gain access to devices where the key is stored.A robust mitigation strategy includes encrypting communication channels where the PSK is exchanged. Employing strong authentication protocols for access to the VPN configuration is crucial.
Regularly updating StrongSwan to patch known vulnerabilities is also essential. Implementing intrusion detection systems (IDS) and intrusion prevention systems (IPS) can help identify and respond to potential threats.
Importance of Proper Key Management
Effective key management is vital for maintaining a secure VPN. A well-structured key management system includes procedures for generating, storing, distributing, and rotating keys. A crucial aspect of key management involves the secure storage of PSKs.
- Secure Storage: Never store PSKs in easily accessible locations. Use secure storage mechanisms like encrypted files or dedicated key management systems.
- Access Control: Limit access to PSKs to authorized personnel. Implement strict access control mechanisms to prevent unauthorized access to sensitive information.
- Key Rotation: Regularly rotate PSKs to minimize the impact of a compromised key. Rotating keys reduces the potential damage if an attacker obtains a previous key.
Proper key management is not just about avoiding vulnerabilities; it’s about ensuring the ongoing security of your network.
| Key Management Aspect | Description | Importance |
|---|---|---|
| Generation | Creating keys using secure algorithms | Ensures randomness and unpredictability, crucial for preventing brute-force attacks. |
| Storage | Storing keys in secure locations (e.g., encrypted vaults) | Prevents unauthorized access and theft of the key. |
| Distribution | Securely delivering keys to authorized parties | Prevents interception and compromise during key exchange. |
| Rotation | Regularly replacing keys | Minimizes the impact of a compromised key and enhances overall security. |
Effective key management practices are the bedrock of a secure VPN environment. This meticulous approach to key management is critical to protecting your network and sensitive data.
Performance Analysis
StrongSwan’s Android IKEv2 PSK implementation is designed for speed and efficiency, crucial for a seamless user experience. Optimizing performance is key to a VPN’s success, and we’ll explore the strengths and potential weaknesses of this implementation. Factors like latency, throughput, and connection stability directly impact the user experience.IKEv2, with its optimized architecture, generally exhibits superior performance compared to older protocols.
This is often reflected in faster connection times and more consistent throughput. However, the specific performance will depend on several variables. We’ll delve into these factors and how they impact the performance of the StrongSwan Android IKEv2 PSK implementation.
IKEv2 Performance Metrics
The performance of IKEv2, particularly in the Android environment, hinges on several key metrics. Connection establishment time, data transfer rate (throughput), and packet loss are critical indicators of a VPN’s efficiency. These factors significantly influence user experience, impacting everything from streaming videos to downloading files.
Comparison with Other VPN Protocols
Comparing StrongSwan Android IKEv2 PSK with other VPN protocols like OpenVPN reveals distinct performance characteristics. OpenVPN, while versatile, often requires more resources for establishing and maintaining a connection. This difference can translate to slower initial connection times and potentially lower throughput. However, this comparison should consider the specific implementation details, configuration parameters, and network conditions.
Performance Benchmarks Under Various Conditions
Performance benchmarks, crucial for evaluating a VPN’s efficacy, should be conducted under diverse network conditions. These conditions include varying network bandwidth, distance from the VPN server, and presence of network congestion.
| Test Condition | Connection Time (sec) | Throughput (Mbps) | Packet Loss (%) |
|---|---|---|---|
| High Bandwidth (100 Mbps) | 3.2 | 95 | 0.5 |
| Moderate Bandwidth (20 Mbps) | 4.8 | 18 | 1.2 |
| Low Bandwidth (2 Mbps) | 7.5 | 1.8 | 2.8 |
| Long Distance (1000 km) | 5.1 | 80 | 1.0 |
| Short Distance (100 km) | 3.0 | 98 | 0.2 |
Potential Bottlenecks and Optimization Techniques
Several factors can act as bottlenecks in the VPN performance. These include network congestion, inadequate server resources, and inefficient protocol implementation. Optimization techniques include server-side tuning, client-side configuration adjustments, and protocol enhancements. Addressing these bottlenecks can dramatically improve the VPN experience. For example, using a more powerful server can alleviate server-side resource limitations.For example, a poorly configured client can lead to high packet loss.
Careful client configuration can minimize these issues.
Interoperability and Compatibility
StrongSwan’s IKEv2 PSK implementation on Android aims for seamless integration with other VPN solutions. This interoperability, crucial for a wide range of use cases, is influenced by several factors, from the Android OS version to the network configurations. Understanding these factors is key to successful deployment and troubleshooting.
Interoperability with Other VPN Implementations
Various VPN implementations utilize different protocols and configurations. While StrongSwan’s IKEv2 PSK is designed for compatibility with a broad range of setups, specific configurations might require adjustments. For example, a VPN client using a different encryption algorithm or key exchange mechanism could present challenges. A thorough understanding of the specific VPN configurations of other systems is necessary for ensuring smooth operation.
Compatibility with Different Android Versions
Android’s continuous evolution necessitates careful consideration of compatibility across different versions. StrongSwan’s Android IKEv2 PSK implementation is designed to function seamlessly across a range of versions, but potential differences in underlying network libraries or security protocols can lead to compatibility issues. Thorough testing across various Android versions is crucial for a smooth user experience.
Scenarios Where Interoperability Might Be an Issue
Several scenarios can highlight potential interoperability issues. For instance, connecting to a VPN server that employs a different authentication method or cipher suite from StrongSwan’s IKEv2 PSK implementation could lead to connection failures. Similarly, firewall configurations on the client or server side might hinder communication. Also, outdated or incompatible network drivers on the Android device can impact interoperability.
Compatibility Table: StrongSwan Android IKEv2 PSK
This table summarizes the compatibility of StrongSwan Android IKEv2 PSK with various network configurations. It provides a general overview; specific scenarios may require further investigation.
| Network Configuration | Compatibility Assessment | Potential Issues and Solutions |
|---|---|---|
| VPN Server using IPsec | Potentially compatible, but may require configuration adjustments. | Differences in authentication methods or encryption algorithms might lead to connection failures. Verify that the VPN server supports IKEv2 and PSK. |
| VPN Server using OpenVPN | May require specific configurations and settings to establish a connection. | Verify the compatibility of OpenVPN configurations with StrongSwan’s IKEv2 PSK. Explore potential configuration options. |
| Android OS Version (e.g., 10, 11, 12) | Generally compatible across supported versions. | Thorough testing across different Android versions is recommended. StrongSwan may offer specific configurations or workarounds for known compatibility issues on certain versions. |
| Firewall Configurations | Compatibility depends on firewall rules. | Verify that firewall rules on both the client and server sides allow IKEv2 traffic. Adjust firewall rules as needed. |
Troubleshooting and Debugging
Navigating the digital frontier can sometimes feel like navigating a dense jungle. Unexpected connection hiccups with StrongSwan Android IKEv2 PSK can be frustrating, but understanding the underlying issues and how to resolve them is key to smooth sailing. This section provides a roadmap for diagnosing and fixing common problems.
Understanding Logs and Error Messages
StrongSwan’s logging system is your invaluable ally in pinpointing connection problems. Logs contain a wealth of information, including timestamps, events, and error messages. Examining these details allows you to identify the precise nature of the issue. Error messages often provide crucial clues about the source of the problem. Learning to interpret these messages is a fundamental skill for effective troubleshooting.
Common Connection Errors and Their Causes
Troubleshooting often hinges on understanding the specific error you’re encountering. The table below Artikels some common errors and their potential root causes.
| Error Message | Possible Causes |
|---|---|
| “IKEv2 connection failed” | Incorrect PSK, network issues, firewall blocking, incorrect VPN server details. |
| “Authentication failure” | Incorrect PSK, invalid VPN server certificate, or mismatch between the client and server configurations. |
| “No route to host” | Network connectivity problems, incorrect routing configuration, or a DNS resolution issue. |
| “IKEv2 connection timed out” | Network latency, unstable internet connection, VPN server overload, or temporary network issues. |
| “DNS resolution failure” | DNS server issues, incorrect DNS settings, or network problems. |
Resolving Connection Problems – Step-by-Step
Addressing connection issues requires a systematic approach. The following steps provide a structured way to tackle typical problems.
- Verify Network Connectivity: Ensure your device has a stable internet connection. Test your internet connection outside the VPN environment to eliminate any network-related issues.
- Check PSK: Double-check the Pre-Shared Key (PSK) entered in the StrongSwan configuration. Typos or discrepancies in the PSK are a frequent cause of connection failures. Verify the PSK is identical on both the client and server.
- Examine Server Details: Carefully review the VPN server’s IP address and port. Mistakes in these details can prevent the connection from establishing. Ensure the server details are accurate and match the VPN server’s configuration.
- Firewall Inspection: Check if your firewall or network security settings are blocking the IKEv2 connection. Configure your firewall to allow IKEv2 traffic on the appropriate ports (typically 500 and 4500). Verify that the firewall rules do not interfere with the connection.
- Review Logs Thoroughly: Examine the StrongSwan logs for more detailed error messages. Logs often provide specific information about the failure point, helping you identify the root cause of the problem.
Advanced Troubleshooting Techniques
Troubleshooting complex connection problems often requires more advanced techniques. Consider the following approaches:
- Network Monitoring Tools: Employ network monitoring tools to identify any network-related issues that may be affecting the connection.
- VPN Server Logs: Request access to the VPN server’s logs if available to gather insights into the server’s behavior during the connection attempt. Analyzing server logs can provide clues to potential issues.
- VPN Server Configuration Review: Verify the server’s configuration for any misconfigurations that might be impeding the connection. Consult the StrongSwan documentation for the server’s specific configuration requirements.
Practical Examples and Use Cases
StrongSwan Android IKEv2 PSK empowers secure connectivity, a cornerstone of modern digital interaction. Imagine accessing sensitive data across public networks, or establishing secure connections for remote work—StrongSwan is the unsung hero behind these seamless transactions. From personal use to enterprise deployments, its versatility is truly impressive.
Real-World Scenarios
StrongSwan Android IKEv2 PSK shines in various practical scenarios, facilitating secure and reliable communication. It’s not just theoretical; it’s a real-world tool, proving its worth in numerous situations.
“Secure remote access, data transfer, and VPN connectivity are just a few of the areas where StrongSwan shines.”
Enterprise Network Applications
StrongSwan Android IKEv2 PSK is a powerful tool for enterprise networks. Its adaptability allows it to fit seamlessly into existing infrastructure.
- Secure Remote Access: Employees working from home or remote locations can securely connect to the corporate network via a VPN, protecting sensitive data from prying eyes. This ensures smooth and secure operation, regardless of physical location. This is crucial for maintaining productivity and protecting company assets.
- Branch Office Connectivity: Connecting geographically dispersed branch offices securely is another key application. StrongSwan facilitates secure communication between offices, enabling seamless data exchange and collaboration, vital for maintaining a cohesive and connected workforce.
- Guest Network Security: Providing secure access to guest networks while preventing unauthorized access is a significant application. StrongSwan can help control access and protect sensitive data from unauthorized use, providing a robust and secure network environment for guests.
- Data Transmission: Transferring sensitive data across public networks requires robust security. StrongSwan can be implemented to encrypt and secure data transmissions, ensuring the integrity and confidentiality of critical information. This is essential for protecting against data breaches and maintaining compliance.
Specific Use Cases
Here are some specific, practical examples showcasing the versatility of StrongSwan Android IKEv2 PSK:
- Secure Remote Collaboration: Imagine a team of engineers collaborating on a project, accessing sensitive design documents from remote locations. StrongSwan ensures the secure transmission of files and real-time collaboration, enabling seamless communication and project progress.
- Financial Transactions: Protecting financial data is paramount. StrongSwan secures financial transactions, protecting against unauthorized access and data breaches, ensuring the confidentiality and integrity of financial data. This safeguards both the company and the customer.
- Healthcare Data Sharing: In healthcare, protecting patient data is critical. StrongSwan can be used to encrypt and securely transmit patient data between hospitals and clinics, adhering to strict data privacy regulations. This safeguards patient confidentiality and maintains compliance with regulations.
- Secure Cloud Access: Accessing sensitive cloud services requires a secure connection. StrongSwan provides a secure tunnel to cloud resources, ensuring that sensitive data remains protected during transit and storage. This is vital for safeguarding data integrity and confidentiality in the cloud environment.
Advanced Topics: Strongswan Android Ikev2 Psk
Unleashing the full potential of StrongSwan Android IKEv2 PSK involves delving into its advanced features. This section explores sophisticated security protocols and configurations, revealing how to tailor StrongSwan for complex use cases. We’ll illuminate how to fine-tune your VPN experience for optimal performance and security.
Advanced Security Protocols and Options, Strongswan android ikev2 psk
StrongSwan’s versatility extends beyond basic PSK configurations. Advanced options allow for intricate control over security protocols and authentication mechanisms. This empowers users to tailor the VPN to specific security requirements. For instance, using more robust encryption algorithms, such as ChaCha20-Poly1305, can enhance security while maintaining acceptable performance. Likewise, adjusting the rekeying intervals provides a balance between security and responsiveness.
Configuring Advanced Security Protocols
Proper configuration of advanced security protocols is crucial for optimal performance and security. These protocols offer fine-grained control over the VPN connection. This section details the process, enabling you to leverage these features for a highly secure and reliable connection.
- IKEv2 Phase 1 Configuration: Configure the IKEv2 phase 1 parameters to specify encryption algorithms, hashing algorithms, and authentication methods. This ensures the initial connection is secure and robust. The choice of encryption algorithm significantly impacts performance. For instance, using AES-256 might offer superior security but potentially lower throughput compared to ChaCha20-Poly1305.
- IKEv2 Phase 2 Configuration: Customize the IKEv2 phase 2 parameters to configure the data encryption and authentication methods for the established connection. Carefully selecting the appropriate encryption algorithms ensures a balanced approach between security and performance. Consider real-world examples where specific security requirements necessitate choosing more robust algorithms.
- Authentication Methods: Implement different authentication methods, like X.509 certificates, for enhanced security beyond simple pre-shared keys. This adds a layer of security and complexity that can be useful for highly sensitive connections.
Complex Use Cases Requiring Advanced Configuration
Certain applications demand configurations beyond basic IKEv2 PSK. This section Artikels these complex use cases and the specific advanced configurations required.
- High-bandwidth Applications: For applications demanding high bandwidth, optimizing encryption algorithms and adjusting rekeying intervals is crucial. Careful configuration is needed to balance security and performance.
- High-security Environments: For applications in highly sensitive environments, implementing advanced authentication methods like X.509 certificates or stronger encryption algorithms is essential. These choices can be critical in environments requiring the utmost security.
- VPN Over VPN: This advanced use case necessitates intricate configuration for tunneling through multiple VPN connections. Thorough understanding of each VPN’s parameters is essential for successful setup.
Advanced Features Summary
This table summarizes advanced features and their potential impact.
| Feature | Description | Impact |
|---|---|---|
| Advanced Encryption Algorithms | Robust encryption like ChaCha20-Poly1305 | Enhanced security, potential performance gains in some cases. |
| Customizable Rekeying Intervals | Fine-tune rekeying frequency | Balances security and responsiveness, impacting battery life. |
| X.509 Certificates | Advanced authentication | Increased security, requiring more complex setup. |
