Entry denied on this server android—a irritating expertise for any developer. This complete information unravels the mysteries behind this frequent error, providing a transparent and concise method to understanding, troubleshooting, and resolving it. We’ll discover the basis causes, from easy community hiccups to intricate safety points, and supply sensible options for varied Android improvement situations.
This information is designed to equip you with the instruments and information to confidently sort out entry denied errors, enabling smoother app deployment and improved person experiences. Whether or not you are a seasoned developer or simply beginning out, this useful resource will empower you to navigate this often-tricky technical panorama.
Understanding the Error
The “entry denied on this server android” error is a standard frustration for builders and customers alike. It signifies a crucial barrier to interplay with a server. This message signifies that your utility or request lacks the mandatory permission to entry the focused server assets. Understanding the basis trigger is important to resolving this problem.
Doable Causes of the Error
The “entry denied” error stems from varied potential points. These can vary from easy configuration issues to extra intricate safety vulnerabilities. In essence, the server is rejecting the connection try as a result of it deems the request unauthorized. Understanding these potential causes permits for extra focused troubleshooting.
Totally different Contexts of the Error
The “entry denied” error can manifest in varied situations, impacting each app improvement and server interactions. This error can seem when attempting to connect with a database, retrieving knowledge from an online service, or interacting with a particular server-side element. For instance, a cellular utility attempting to entry a protected API endpoint would possibly encounter this error.
Potential Causes and Options
The desk under Artikels varied potential causes for the “entry denied” error and gives corresponding troubleshooting methods.
| Cause | Signs | Typical Options |
|---|---|---|
| Incorrect Credentials | The appliance or request makes an attempt to attach with invalid login particulars. | Confirm and proper the supplied username and password or API key. Double-check the format and case sensitivity of the credentials. Make sure the credentials are present and legitimate. |
| Inadequate Permissions | The appliance or person lacks the mandatory entry rights to the requested useful resource. | Guarantee the appliance or person has the required permissions to entry the useful resource. Confirm if the API key or authentication token is related to the right degree of entry. |
| Community Connectivity Points | Issues with the community connection between the consumer (your utility) and the server. | Examine the web connection and troubleshoot any community points. Confirm the server’s availability and accessibility. |
| Server Configuration Errors | The server might need misconfigured safety settings that forestall the appliance’s connection. | Contact the server administrator for help in resolving any server configuration errors. Evaluate server logs for extra detailed error messages. |
| Firewall Restrictions | Community firewalls may be blocking the connection request from the appliance. | Regulate firewall settings to permit communication between the consumer and the server. Seek the advice of your firewall documentation for steering. |
Troubleshooting Steps

Unveiling the mysteries behind the “entry denied” error usually requires a scientific method. This entails understanding potential causes and implementing focused options. Success hinges on methodical investigation and cautious evaluation of the state of affairs.This information gives a structured path to resolving entry denial points in your server, empowering you to swiftly determine and tackle the basis trigger. It is designed to be sensible and easy, main you thru every step with clear directions and anticipated outcomes.
Figuring out the Root Trigger, Entry denied on this server android
Pinpointing the exact motive for the “entry denied” error is essential for efficient troubleshooting. This entails a cautious examination of permissions, configurations, and person accounts. Analyzing system logs and monitoring actions gives precious insights. By systematically analyzing varied facets, the basis trigger could be remoted.
Frequent Causes and Options
A wide range of components can contribute to the “entry denied” error. Understanding these potential causes and their corresponding options is important.
- Incorrect Consumer Credentials: Make sure the username and password are correct. Typos or case sensitivity points can result in this error. Confirm the credentials are appropriately entered.
- Inadequate Permissions: The person account won’t have the mandatory permissions to entry the requested useful resource. Evaluate and modify permissions to grant acceptable entry.
- Community Connectivity Issues: Issues with community connections can block entry to the server. Examine for community connectivity points and tackle any associated issues.
- File System Points: Corrupted or lacking information within the file system may cause errors. Guarantee the mandatory information and directories exist and are accessible.
- Server Configuration Errors: Misconfigurations throughout the server’s settings can forestall entry. Evaluate and proper any configuration errors to allow entry.
Troubleshooting Process
A scientific method is vital to resolving “entry denied” points. This structured process guides you thru the steps required for efficient troubleshooting.
| Step | Motion | Anticipated End result | Doable Points |
|---|---|---|---|
| 1 | Confirm Consumer Credentials | Profitable login | Incorrect username/password, incorrect case, community points |
| 2 | Examine Consumer Permissions | Acceptable permissions granted | Inadequate privileges, incorrect group assignments |
| 3 | Examine Community Connectivity | Steady community connection | Community outages, firewall points, router issues |
| 4 | Evaluate File System Integrity | Information and directories accessible | Corrupted information, lacking information, incorrect paths |
| 5 | Study Server Configurations | Configurations match necessities | Incorrect settings, outdated configurations |
Community and Server Configuration
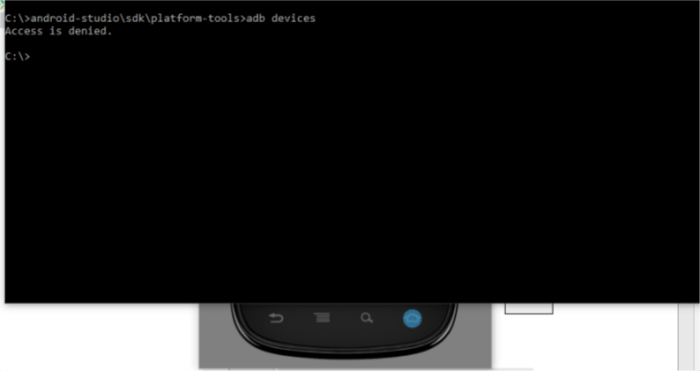
Generally, the “entry denied” message is not about you; it is concerning the community and server’s settings. It is like attempting to enter a constructing with the fallacious key or by means of a locked door. Understanding these configurations can pinpoint the issue and open the door to options.Community configurations play an important position in figuring out who can entry what assets on a server.
Incorrect configurations, like mismatched usernames or incorrect IP addresses, can result in entry being denied. Server-side configurations, comparable to firewall guidelines, person permissions, and authentication strategies, are equally vital. They act as gatekeepers, making certain solely licensed customers can acquire entry. Equally, community protocols outline the language of communication between your gadget and the server. Mismatches or vulnerabilities in these protocols may end in entry denials.
Community Configuration Checks
Correct community configurations are important for seamless communication between shoppers and servers. Incorrect configurations can result in the dreaded “entry denied” error. This part Artikels a scientific method to confirm community configurations.
| Configuration Setting | Anticipated Worth | Difficulty Detection | Remediation |
|---|---|---|---|
| IP Deal with | Legitimate, distinctive IP tackle assigned to the gadget | Incorrect or duplicate IP tackle; battle with community units | Confirm IP tackle project, guarantee no conflicts exist, and acquire a sound IP tackle from the community administrator. |
| Subnet Masks | Matching subnet masks for the community | Mismatch between gadget and community subnet masks | Confirm the subnet masks assigned to the gadget matches the community subnet masks. |
| Default Gateway | Legitimate gateway tackle for the community | Incorrect or unavailable gateway tackle | Make sure the gadget’s default gateway is appropriately configured to entry the community router. |
| DNS Server | Legitimate DNS server tackle | Invalid or unavailable DNS server tackle | Examine the DNS server configuration for validity and availability. |
| Firewall Guidelines | Permitting entry to the required companies | Blocking entry to the mandatory companies by firewall guidelines | Regulate firewall guidelines to allow communication with the server. |
| Port Numbers | Appropriate port numbers for the companies | Incorrect or blocked port numbers | Confirm the right port numbers for the required companies and guarantee they don’t seem to be blocked by the firewall. |
Server-Aspect Configuration
Server-side configurations are like a fortress’s partitions and gates, guarding the assets inside. Accurately configured servers are important for safety and clean operation.Server-side configurations, together with person permissions, authentication mechanisms, and firewall guidelines, are crucial for limiting entry to assets. If these settings are incorrect, the “entry denied” message seems. An important step is checking the person’s permissions on the server to make sure they’ve the mandatory rights to entry the specified assets.
Additionally, the authentication strategies utilized by the server ought to be verified for proper implementation and compatibility with the consumer. Incorrect configurations can result in denial of entry.
Community Protocols
Community protocols are like a standard language for communication between your gadget and the server. Totally different protocols deal with totally different duties, and mismatches or points in these protocols may cause entry denial.Varied community protocols, like TCP/IP, HTTP, and FTP, facilitate communication between units. Issues with these protocols can result in entry denial points. Understanding how these protocols work together with one another and with the server’s configurations is essential.
For instance, an HTTP request may be blocked by a misconfigured firewall, resulting in an entry denied message. Troubleshooting such points requires a cautious examination of the community protocols concerned.
Software-Particular Points
Android apps, like tiny, intricate machines, depend on intricate permission methods to function. Generally, a seemingly minor hiccup in how these permissions are dealt with can result in the irritating “entry denied” error. Let’s delve into the potential pitfalls throughout the utility itself.
Permission Fundamentals
Android’s permission system is designed to safeguard person knowledge and privateness. Purposes should explicitly request permissions for particular functionalities, like accessing the digital camera, storage, or community. These permissions are crucial; with out them, your app will not have the ability to perform as supposed. Denial of a required permission can result in an entry denied error. Consider it like a locked door; you want the right key (permission) to enter (entry).
Improper Permission Dealing with
An important side of creating sturdy Android apps is cautious dealing with of permissions. Mismanaging these requests can result in the dreaded “entry denied” message. As an illustration, requesting permissions on the fallacious time, failing to deal with person denials, or not appropriately checking for permission standing can all consequence on this error. Permissions aren’t a one-time request; the app must examine for his or her standing periodically.
Think about a traveler needing a visa for a rustic; the appliance should affirm the visa is lively and legitimate for entry.
Frequent Software-Degree Causes
Understanding the basis causes of entry denied errors could be essential to fixing them. Under, a desk highlights frequent application-level causes, their descriptions, illustrative code snippets, and options.
| Trigger | Description | Instance Code Snippet | Resolution |
|---|---|---|---|
| Incorrect Permission Request | The appliance requests the fallacious permission, or the permission isn’t wanted for the operation. | requestPermissions(new String[] "android.permission.CAMERA", 1); (Wants android.permission.READ_EXTERNAL_STORAGE as a substitute) |
Guarantee the right permissions are requested based mostly on the performance. |
| Incorrect Permission Dealing with | The appliance fails to deal with the person’s permission determination appropriately, or doesn’t examine for permission standing. | if (ContextCompat.checkSelfPermission(this, Manifest.permission.CAMERA) != PackageManager.PERMISSION_GRANTED) (Lacking code to deal with permission granted/denied consequence) |
Implement correct conditional logic to deal with granted and denied permissions, and examine standing in strategies that require the permission. |
| Permission Denial at Runtime | The person denied the permission beforehand, and the appliance doesn’t deal with the denial correctly. | if (ActivityCompat.shouldShowRequestPermissionRationale(this, Manifest.permission.ACCESS_FINE_LOCATION)) (No dealing with of permission denied.) |
Implement a rationale to clarify why the permission is critical and request once more, with acceptable UI parts. |
| Incorrect Context Utilization | Utilizing the inaccurate context (e.g., Exercise as a substitute of Service) for requesting permissions. | Requesting permission in a Service, however utilizing an Exercise’s context. | Use the suitable context for requesting permissions. |
Code Examples and Options

Unveiling the secrets and techniques behind “entry denied” errors is like fixing a digital thriller. Understanding the code’s logic and the server’s response is essential to pinpoint the issue. This part delves into sensible code examples and options for varied Android improvement situations.The “entry denied” error in Android improvement usually stems from misconfigurations, improper permissions, or defective community communication. Correcting these points requires a deep dive into the code, and these examples will illuminate the trail ahead.
Java Code Instance: Community Request
Java’s networking capabilities, coupled with Android’s particular context, usually kind the center of the issue. Here is a code snippet demonstrating a community request:“`javaimport java.io.IOException;import java.internet.HttpURLConnection;import java.internet.URL;public class NetworkRequestExample public static void essential(String[] args) attempt URL url = new URL(“your_server_url”); HttpURLConnection connection = (HttpURLConnection) url.openConnection(); connection.setRequestMethod(“GET”); connection.join(); int responseCode = connection.getResponseCode(); if (responseCode == HttpURLConnection.HTTP_OK) // Course of profitable response else // Deal with error (entry denied possible right here) System.out.println(“Error: ” + responseCode); System.out.println(“Server response: ” + connection.getResponseMessage()); catch (IOException e) e.printStackTrace(); “`This instance highlights how one can deal with potential community errors.
Discover the essential step of checking the response code; a non-200 code usually signifies an issue, together with “entry denied.”
Kotlin Code Instance: Dealing with Permissions
Kotlin’s concise syntax and Android’s permission system make it easy to deal with authorization points. An important side of dealing with permissions entails requesting particular permissions dynamically at runtime.“`kotlinimport android.Manifestimport android.content material.pm.PackageManagerimport androidx.core.app.ActivityCompatimport androidx.core.content material.ContextCompat// … inside your Exercise or Fragment …personal enjoyable checkAndRequestPermissions() val permissions = arrayOf(Manifest.permission.INTERNET) val permissionCheck = ContextCompat.checkSelfPermission(this, permissions[0]) if (permissionCheck == PackageManager.PERMISSION_GRANTED) // Permission granted, proceed along with your code else ActivityCompat.requestPermissions(this, permissions, 123) // Request permission override enjoyable onRequestPermissionsResult(requestCode: Int, permissions: Array , grantResults: IntArray) if (requestCode == 123) if (grantResults.isNotEmpty() && grantResults[0] == PackageManager.PERMISSION_GRANTED) // Permission granted, proceed along with your code else // Permission denied. Deal with appropriately. // Present an acceptable message to the person, maybe guiding them to the settings. “`This demonstrates how one can examine for web permissions, a standard requirement for community requests. Critically, it exhibits how one can deal with permission requests and responses.
Totally different Programming Languages
Varied programming languages, together with Java, Kotlin, and others, are generally used for Android improvement. The rules for dealing with entry denied errors are largely related throughout languages, with the first concentrate on error dealing with, permission checks, and safe communication.
Illustrative Situations: Entry Denied On This Server Android
Navigating the digital world generally looks like a treasure hunt, the place you are trying to find the elusive key to unlock the subsequent degree. The “entry denied” error is sort of a irritating roadblock, however understanding the situations behind it could possibly make the journey smoother. This part particulars varied conditions the place this error pops up, providing clear explanations and options.The “entry denied” error is not a thriller; it is a message telling you that your request to entry one thing (a file, a community useful resource, or an utility) has been rejected.
It indicators a mismatch between your credentials and the necessities for entry. These situations reveal the precise circumstances that set off this error.
Incorrect Credentials
It is a easy state of affairs. You are attempting to entry one thing, however the supplied username or password is fallacious. That is like attempting to open a locked door with the fallacious key. The system, understandably, does not grant you entry. A typical repair is to double-check the login particulars.
Errors occur; re-entering the right info usually resolves the problem. In the event you suspect a compromised account, change your password instantly and report it to the suitable authorities.
Community Connectivity Issues
Think about a bridge connecting your gadget to a server. If the bridge is damaged, you may’t attain the vacation spot. Community points, comparable to a poor web connection, a firewall blocking the connection, or a community outage, can forestall entry. Troubleshooting community connectivity is essential. Checking for a steady web connection, verifying firewall settings, and making certain community connectivity are important steps.
Server Overload
Think about a busy restaurant. If too many purchasers attempt to order concurrently, the kitchen would possibly develop into overwhelmed. Equally, a server overloaded with requests can deny entry to new requests. If the server is experiencing excessive load, the answer is to attend for the system to get well or contact the server administrator. This often resolves itself.
Useful resource Limitations
Think about a library with a restricted variety of books. If the variety of accessible books is exhausted, new requests can’t be fulfilled. Equally, servers have finite assets (like space for storing or processing energy). If the useful resource you want is unavailable, the system denies entry. If the limitation is non permanent, the entry might be granted as soon as the useful resource is freed up.
Software-Particular Errors
Consider an utility as a fancy machine. If part of the machine is malfunctioning, all the machine won’t work as anticipated. Generally, particular configurations throughout the utility itself can set off entry denied errors. These points may be associated to permissions, file paths, or inner inconsistencies throughout the software program. Seek the advice of the appliance’s documentation or assist channels for steering.
File Permissions Points
Think about a file protected by a lock. Solely licensed customers can unlock and entry the file. In case your account does not have the mandatory permissions, the system denies entry. Correcting file permissions entails understanding and adjusting the entry rights for the file or listing.
Authentication Timeout
Consider a safety gate. In the event you do not enter the right code inside a particular time-frame, the gate closes. Equally, if the authentication course of takes too lengthy, the server would possibly day out, resulting in an entry denied error. Confirm the server settings and guarantee a steady connection to stop timeouts.
